
Proactive Cyber Defense
for Your Business
Our managed security service team provides round-the-clock protection to safeguard your data and reputation.
Ransomware attacks, data theft, and system infiltration are rising, demanding robust and proactive security measures. Our Managed Security Service (MSS) acts as your vigilant shield, providing 24/7 protection against these threats. We minimize risk, ensure compliance, and safeguard your critical assets. Partner with us to build a resilient cyber defense and focus on growing your business with confidence.
Our clients’ experiences highlight our commitment to excellence.

I think Clint is an excellent resource. I usually will tell him to keep graduating from his current post and move up to the next level and he will always do. He has the right attitude and discipline - i love working with him and i get the same feedback from our other colleagues.

Veron Tiong
Marketing Director

I appreciate Charlene's proactiveness to ask questions on topics that are not clear for her. This reflects her attitude to learn more about the application and processes that she supports. She can support morning checks and requests with minimal to no supervision. For continuous improvement in terms of log checking and issues analysis. Always check previous cases (emails and chat), logs, Autosys, recordings and procedure. On spare time, she can check procedures that she has not yet encountered due to minimal ticket count. Also, she can simultaneously do tickets and not wait for the other to finish since some requests take time due to copying of files so as not to waste time especially on busy days. Lastly, it would be good if she can take some topic on Udemy regarding SQL.

Charish Adove
Marketing Director

Nikko is easily one of the best developers I have worked with in my 15 years as a software engineer.

Ryan Lang
Marketing Director

Bong's overall performance is really commendable, and he is excellent in his work. I can rely on him for all tasks with minimal supervision. He puts in his best effort for every task assigned to him and strives to improve. Bong is attentive to instructions and is also capable of providing valuable opinions. I genuinely hope to have the opportunity to work with him again in the future. I believe this feedback will contribute to him being recognized and given more opportunities by Xurpas to grow in his career.

Glaiza Guison
Marketing Director

She is very reliable and hard-working.

JB Tiamson
Marketing Director

I admire Kent's eagerness to learn. He's also reliable, he can work with minimal supervision.

Conchui Perez
Marketing Director

MJ works fast and the quality of his builds is impressive. He is respectful of his other teammates' time by attending important sessions on time. He can work with anyone in the team with ease and comfort.

Froilan Tatoy
Marketing Director

I love working with Jumera. She delivers great work and helps me to move things forward nicely. She has had some time off sick, but I'm putting this down as her working hard to deliver items for us and it having an impact on her, so I'm not holding that against her. Thank you Jumera for your excellent work.

Doug McPhee
Marketing Director

I love working with Jumera. She delivers great work and helps me to move things forward nicely. She has had some time off sick, but I'm putting this down as her working hard to deliver items for us and it having an impact on her, so I'm not holding that against her. Thank you Jumera for your excellent work.

Doug McPhee
Marketing Director
In the modern business landscape, cyberattacks are a constant threat, impacting organizations of every scale and sector. Data breaches compromise sensitive customer information, and ransomware attacks can disrupt operations entirely. The financial fallout and damage to your reputation can be severe.
Don't become another statistic. Our Managed Security Service offers proactive, around-the-clock protection against the ever-changing landscape of cyber threats. We merge advanced technology with the knowledge of experienced security experts to protect your valuable assets, reduce risk, and guarantee compliance.
Concentrate on expanding your business with assurance, knowing your cybersecurity is expertly managed.
How We Protect Your Business

Log Management & Threat Detection
Real-time monitoring of system logs to detect and prevent cyberattacks. Secure log storage for compliance and forensic investigations.

Firewall Compatibility
Works with any firewall that supports syslog.

Endpoint Security
Protect your devices from malware, ransomware, and unauthorized access with our advanced endpoint protection.

Continuous Monitoring & Threat Hunting
Our security experts actively search for vulnerabilities and potential threats 24/7 to safeguard your network.

Ransomware Defense
Stay ahead of ransomware attacks with our robust defense strategies and data protection measures.

Simple Implementation
Automated log transfer set by your staff and installing open-source, lightweight sysmon app on your designated devices.

System Independence
We provide detection and recommended remediation advice to your staff, so there is never any outside operation.
The Advantages of Partnering with Us

Reduced Risk Of Cyber Attacks
Proactive threat detection and neutralization.

Faster Incident Response
Immediate expert response minimizes downtime.

Counter-Measure for Insider Threats
Easily adjust your workforce to meet fluctuating project demands.

Improve Security Posture
Strengthen defenses against evolving cyber threats.
Reduce cost
Cost-effective, expert security without in-house overhead.

Peace of Mind
Focus on growth, knowing your security is in expert hands.
Resource Hub
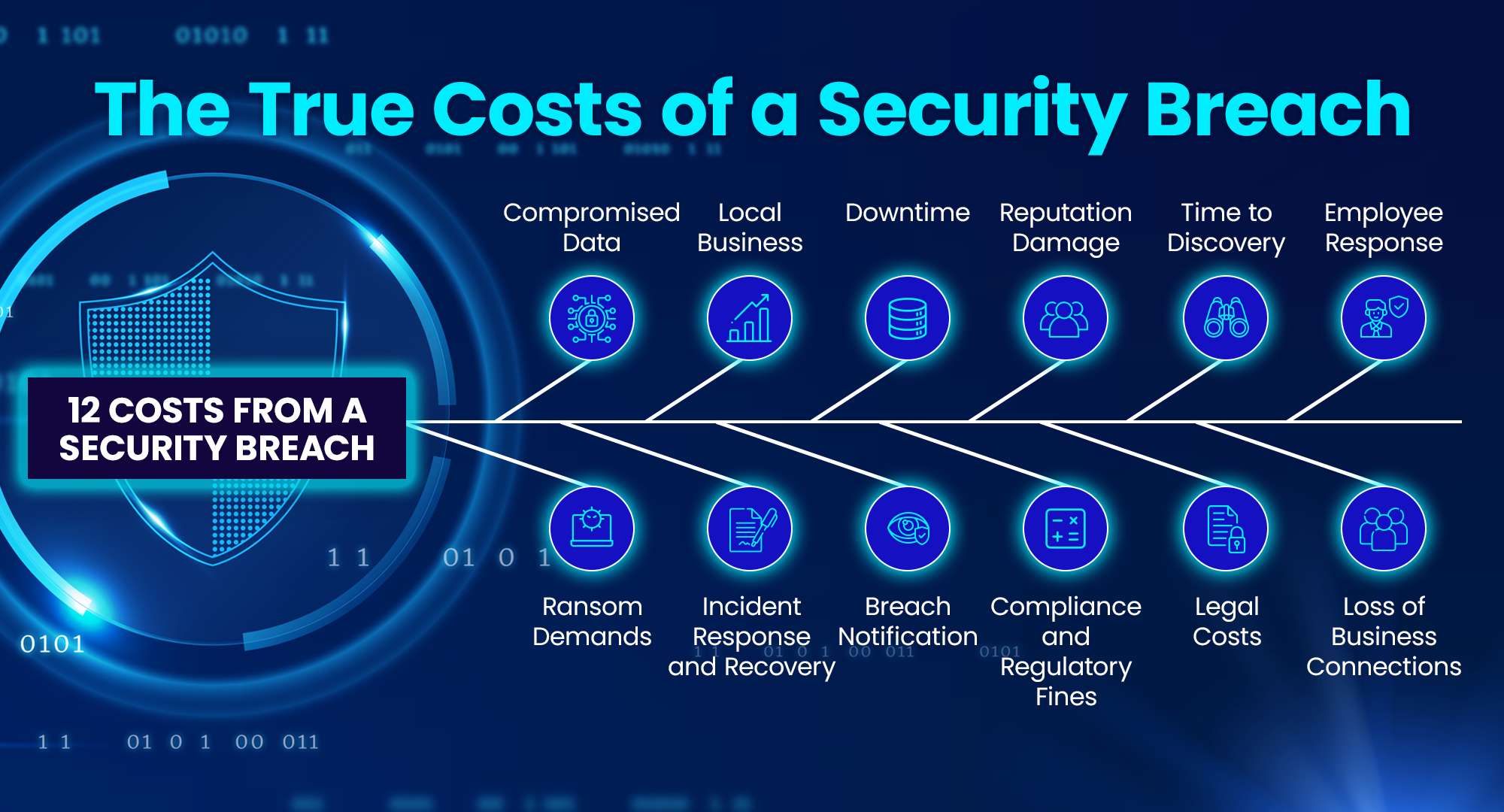
Cyberattacks are a constant threat to businesses of all sizes. While the immediate financial losses from a breach are significant, the ripple effects can be even more devastating. Let’s explore the hidden costs that can cripple your business and how managed security services can provide a crucial line of defense.
Key Benefits of IT Staff Augmentation
- Ransom Demands
One of the most immediate impacts of a cyberattack is the potential for ransom demands. Cybercriminals may encrypt critical data and demand payment in exchange for decryption keys. These demands can be exorbitant, and paying them does not guarantee that data will be fully restored. Managed security services can help prevent these attacks and provide strategies to mitigate their impact. - Compromised Data
Data breaches can lead to the exposure of sensitive information, including customer details, financial records, and proprietary data. The loss of such information can have severe repercussions, including identity theft and loss of competitive advantage. Protecting data through robust cybersecurity measures is essential to prevent unauthorized access. - Incident Response and Recovery
Once a breach occurs, the cost of incident response and recovery can be significant. This includes detecting the breach, containing the threat, eradicating malicious actors, and restoring systems to normal operation. A well-prepared incident response plan, supported by managed security services, can dramatically reduce recovery time and costs. - Lost Business
The aftermath of a breach can lead to immediate and long-term loss of business. Customers may lose trust in the company's ability to protect their data, leading them to switch to competitors. The financial impact of lost business can be substantial, emphasizing the importance of robust cybersecurity measures. - Breach Notification
Organizations are legally required to notify affected parties and regulatory bodies of a data breach. The process of breach notification can be complex and costly, involving communication with customers, stakeholders, and authorities. Managed security services can ensure compliance with notification requirements and streamline the process. - Downtime
A security breach often results in significant downtime, during which business operations are disrupted or halted. This downtime can lead to lost productivity and revenue. Implementing strong cybersecurity measures can minimize the risk of such disruptions and ensure business continuity. - Compliance and Regulatory Fines
Failure to comply with data protection regulations can result in hefty fines and penalties. Organizations must adhere to standards such as GDPR, HIPAA, and others to avoid legal repercussions. Managed security services can help ensure compliance with these regulations, reducing the risk of fines. - Legal Costs
Legal expenses can quickly escalate in the wake of a data breach. Organizations may face lawsuits from affected parties, and the cost of legal representation can be substantial. Preventative cybersecurity measures can help avoid these legal entanglements.
Damage to Your Reputation and Relationships
- Reputation Damage
A breach can tarnish your brand image, making it difficult to regain customer trust and loyalty. - Loss of Business Connections
Strained relationships with partners and suppliers can disrupt your supply chain and operations. - Employee Morale
The stress and uncertainty of a breach can impact employee productivity and morale.
The Longer it Takes, the Worse it Gets
- Time to Discovery
The longer a breach goes undetected, the more damage can be done.

Protect Your Business with Managed Security Services
The consequences of a security breach are severe and far-reaching. To safeguard your business from these threats, a robust cybersecurity strategy is essential. Managed security services offer a comprehensive approach to protecting your organization from cyberattacks. By partnering with a trusted managed security service provider, you can gain access to expert knowledge, advanced technologies, and round-the-clock monitoring to mitigate risks and protect your valuable assets.
Managed security services provide a comprehensive solution:

24/7 Monitoring and Threat Detection
Identify and neutralize threats before they cause damage.

Expert Incident Response
Minimize the impact of a breach with swift and effective action.

Proactive Security Measures
Strengthen your defenses against evolving cyber risks.

Compliance and Regulation Adherence
Avoid costly fines and penalties.

Peace of Mind
Focus on your core business, knowing your cybersecurity is in expert hands.
By understanding the true costs of a security breach, you can make informed decisions about your organization’s cybersecurity posture. Don’t wait until it’s too late. Take proactive steps to protect your business today.
Don’t let a security breach cripple your business. Contact us today to learn how our managed security services can help you safeguard your organization.
FAQs
A Managed Security Service (MSS) provides continuous monitoring, management, and security defense for your enterprise’s IT infrastructure, often through an outsourced security provider. We operate as an alert and analysis team, leveraging our advanced artificial intelligence system to work with your IT team for proactive action. We never require access or control over your systems.
Enterprises facing increasingly complex cyber threats can benefit from MSS, especially those handling financial transactions, confidential data, or personal information. Any business that cannot operate for more than a week without computer systems should consider dedicated cybersecurity.
We prioritize prevention by minimizing the risk of unauthorized access. If a breach occurs, we work with global internet service providers to revoke hacker access, preserve data for analysis and forensic purposes, and provide evidence to law enforcement. Our comprehensive incident response plan ensures swift containment and mitigation. Our MSS partner will collaborate closely with you to minimize damage and restore normal operations.
Yes, our solutions adhere to industry best practices and comply with relevant regulations to ensure the highest level of security.
We provide daily and weekly “ACTION NEEDED” alerts to your IT team, along with proposed remedies. For management, we offer reports comparing historical trends of cyber intrusion to help manage IT resources and priorities.
Yes, our team is available around the clock to address any security concerns or incidents.
We will handle your cybersecurity, including monitoring, threat detection, and incident response. Your team is responsible for timely execution of the remedies we provide to address detected security breaches.
Our pricing is flexible and depends on your specific business needs. We will provide a customized quote after assessing your requirements.
You can contact our support team through phone, email, or live chat for immediate assistance.
Yes, we provide alerts and remedies to your IT team without needing access or control of your system. There are no integration issues as we analyze system-generated logs and minimize intrusion to your technical infrastructure and operations.
Yes, MSS solutions are designed to scale with your business, ensuring continued security coverage as your enterprise grows and your infrastructure evolves. MSS can increase growth velocity by reducing downtime and risk.
Yes, we never have control over your security policies and technical assets. MSS works collaboratively with your internal team, offering monitoring and expertise while your IT team controls the technology and decision-making.
MSS providers often offer dedicated incident response teams that can investigate, contain, and mitigate threats quickly, minimizing damage and reducing response times.
Yes, our MSS provider offers cloud security services that protect cloud-based infrastructures, ensuring secure configuration, monitoring, and threat response for public, private, and hybrid clouds.
Our MSS partner analyzes anonymized log data generated from computer systems and does not have access to confidential data. Your IT grants access to publicly known log systems and uses only open-source software, maintaining data control. Internally, we implement strict security protocols, including encryption, access controls, and regular audits.
Our MSS partner can monitor traffic connecting to your server and employee devices, ensuring documentation of interactions and detecting malicious traffic.
Yes, MSS providers often offer vulnerability management services, including regular scanning and patching of vulnerabilities to reduce exposure to threats.
Yes, MSS providers deploy insider threat detection mechanisms that monitor unusual or suspicious activities by employees or contractors within your network. We can monitor USB drive insertion, file exfiltration, and unauthorized software installations.
Our managed cybersecurity services package offers comprehensive protection, including:
Log Management & Threat Detection, Firewall compatibility, Endpoint Security, Continuous Monitoring & Threat Hunting, Ransomware Defense, Simple implementation, System Independence
Contact
Concerned about Security breaches?
Our experts are ready to help you build a resilient security strategy. Let’s discuss how we can protect your data and your peace of mind.
Why trust Xurpas?
requirements through an open, consultative, and collaborative process. This transparency
ensures we offer the best available solution tailored to fit your timeline and budget.
Experience unparalleled expertise and customer-centric solutions with Xurpas.

